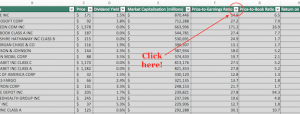
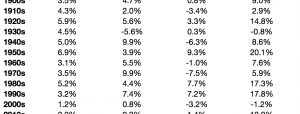
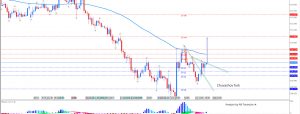
WikiLeaks is at it again—this time pulling back the curtain on how the CIA conducts much of its spy business. If you‘ve been afraid that Big Brother has been watching you, then these latest revelations will do nothing to ease your concerns. The spy business is big business, and now more than ever its technologically-driven tentacles are reaching deep into our everyday lives.
However, it goes far beyond that. Not only do governments around the world exploit technologies and applications for the purpose of gathering intelligence, they are also building up their expertise and cyberlibraries to wage war in cyberspace. For the past several decades, most people believed that World War III would likely end in nuclear devastation or a biochemical apocalypse. However, there is a very real possibility that the next major global conflict will be fought in cyberspace, and the outcome will be a function of an entity’s ability to defend itself from cyber attacks.
Yesterday (March 7, 2017), WikiLeaks published 8,761 files it dubbed “Vault 7” that allegedly belong to the CIA’s Center of Cyber Intelligence. Many people around the world question the motivation, objectives, and procedures of the WikiLeaks organization. However, to date, none of its published leaks has ever been disproven. Comparing yesterday’s data release to the Edward Snowden leaks of classified information in 2013, the Wall Street Journal said, “In one sense. Mr. Snowden provided a briefing book on U.S. surveillance, but the CIA leaks could provide the blueprints.”
WikiLeaks stated it was not publishing the source code of the various spy tools (at this time), but they did identify many specific programs and applications that infiltrate the global positioning, voice, and data features of smartphones. They also have programs that allow some internet-connected Samsung TVs to be used as listening devices, and with its vast library of malicious programs, they can make hacks appear to come from other countries.