Rodeo Finance, a DeFi protocol residing on the Arbitrum blockchain, suffered its second significant exploit on July 11, resulting in a loss of 472 ETH, equating to approximately $888,000 million. The exploit was orchestrated through a code vulnerability within Rodeo’s Oracle.
The exploiter transferred the stolen funds from Arbitrum to Ethereum and then swapped 285 ETH for unshETH, according to data shared by PeckShield, a blockchain analytics firm. Following the swap, the exploiter deposited ETH into Eth2 staking before sending 150 ETH to Tornado Cash, a mixer service used frequently to obfuscate the transaction trail.
PeckShield later confirmed that the amount was 472 ETH, equalling $888,000, confirming a recalculation:
Correction: the total loss w/ 472 $ETH (~$888K)
The exploiter swapped 285 $ETH for $unshETH and bridged them back to #Arbitrum to continue the hackhttps://t.co/wmlQ7pJlKV
— PeckShieldAlert (@PeckShieldAlert) July 11, 2023
The exploit was performed using a strategy involving time-weighted average price (TWAP) oracle manipulation, a tool used by DeFi protocols to average out the price of an asset over a given period, thereby reducing the risk of market volatility. This method, however, has been identified as a potential vulnerability.
The exploiter started by borrowing a substantial amount of an asset, after which they manipulated the price downward, enabling them to purchase the same asset at a significantly reduced price. This allowed the exploiter to pay off the loan and gain a profit from the lower price they managed to set through their manipulations.
This latest breach has had a profound impact on Rodeo Finance, causing the total value locked (TVL) to nosedive from $20 million to less than $500.
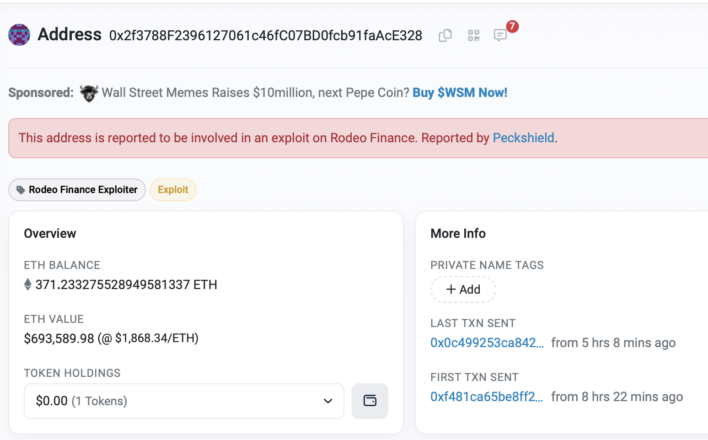
The wallet address tied to the exploit is still in possession of over 370 ETH and has been flagged by Etherscan as connected to the Rodeo exploit.